Scan Type
There are basically two types of Scans –
1. Passive Scan: The attacker cannot be recognized by the target,
it is just like a Smelling.
To monitor the Network Traffic we can use Tcpdump and Wireshark
2. Active Scan: In active scan attacker or pentester can be recognized by the target because it leaves traces that are likely to alert the target or produce evidence against him, it is just like Tasting.
To send packets we can use Nmap, Hping, Scapy , Ping, tracert, etc..
Nmap
Nmap is (Network Mapper) is a free and open-source powerful utility for network discovery and security auditing which is well-designed documentation and platform-independent.
It can do :
1. Host detection (ping scan)
2. Port scanning (syn,tcp,udp)
3. Service and version detection
4. Operating system detection
5. Firewall detection
6. Vulnerability assessment
7. Brute force attacks
8. Exploitation
9. Script scan
10. Timing and many more
And Nmap has its own scripting engine it allows developers to develop new modules.
**Scan Types**
Ping Scan (No Port Scan) ( -sn | -sP )
Detecting Live Hosts:
It only prints out the available hosts who respond to the host discovery probes.
Nmap -sn a default behavior for the privileged user which sends
* ICMP echo request
* SYN →TCP 443 port
* ACK →TCP 80 port
* ICMP timestamp request
For the Unprivileged User which only sends
* SYN →TCP 80, 443 ports
when a privileged user tries to scan targets on a local ethernet network ARP request is used unless-send-ip was specified
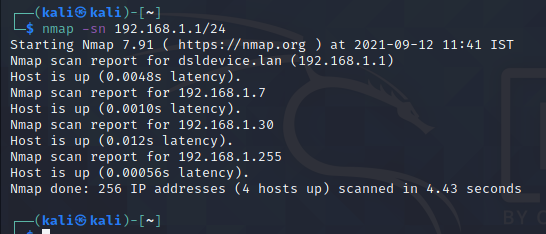
The most basic Port Scan Types
SYN Scan ( -sS )
Port scan with Nmap allows us to discover which TCP or UDP ports are open on your target host. Network ports are the entry points to a machine that is connected to the Internet.
A service that listens on a Port is able to receive data from a client application, process it, and send a response back. Malicious clients can sometimes exploit vulnerabilities in the server code so they can gain access to sensitive data or execute malicious code on the machine remotely.
That is why testing for all ports is necessary in order to achieve a thorough security verification. Port scanning is usually done in the initial phase of a penetration test. In order to discover all network entry points into the target system.
It can be performed quickly by scanning thousands of ports per second on a fast network not blocked by restrictive firewalls. It’s also relatively stealthy since it never completes TCP connections.


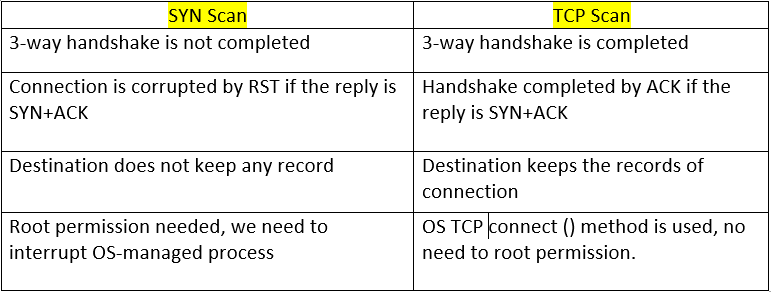
When we send a syn packet, the destination system replies a syn ACK packet to show that it’s ready for a connection and we send RST to corrupt the handshake, and the map interprets this result as the Port is open.
If the destination system replies to an RST packet for our SYN packet, that means the Port is accessible, but it’s close.
If the destination system doesn’t respond to our SYN packet then Nmap thinks that the packet is dropped or filtered. It’s a common behavior of firewalls.
If the destination system replies an ICMP unreachable packet for us in packet again, it’s interpreted as filtered. This is another type of firewall behavior.

TCP Scan (-sT)
TCP scan, also known as TCP Connect scan. It is the default TCP scan type When sin scan is not an option, well, when is this is not an option.
The user does not interfere with a TCP three-way handshake the whole process is managed by the operating system itself.
doesn’t need to be a privileged user to perform TCP Connect scans.

The steps of the TCP Connect scan are exactly the same as the TCP three-way handshake.

SYN Scan Vs TCP Scan


UDP SCAN (-sU)
Takes a long time (timeouts)
•Some important ports: DNS (53), TFTP (69), DHCP (67–68), NTP (123), SNMP (161–162)
•Sends empty UDP packets in general.
•Should run with version detection option for more accurate results.


Terms- Port Statements
IF OPEN
• Port is accessible
• A service is listening to the port
IF CLOSED
• Port is accessible
• Nothing is filtering the port: Firewall etc.
• No service is listening to the port
• Example: Host sends back an RST flag
IF FILTERED
• No answer
• Filtered by a security system e.g. Firewall
• Port might be open or closed
OPEN I FILTERED
• i.e. UDP scan
• No answer
• Might be filtered by a security system e.g. Firewall
• Application may not be responding






Hey! This post couldn’t be written any better! Reading through this post
reminds me of my previous room mate! He always kept chatting about this.
I will forward this post to him. Pretty sure he will have a good read.
Many thanks for sharing!
Sure .. Thanks
Everything is very open with a very clear description of the challenges. It was really informative. Your site is very helpful. Many thanks for sharing!
I want to to thank you for this wonderful read!! I absolutely loved every little bit of it. I have you saved as a favorite to look at new stuff you postÖ